Learn more about our highly effective process

Workshop
When the customer is planning to lunch a new product, there are multiple hypotheses from sales, product and R&D departments how it should look like and which traits it should accommodate. In the Workshop phase, CoreWillSoft is bringing its market-wide experience to challenge and complement the product concept as a whole.
Business Analysis
The following Business Analysis is aimed to verify the most essential functionality of the product for the target customer group. Often it can result in a variation of configurations or even different solutions for dedicated customer groups.


Requirements
Requirements phase exactly defines product parameters and matches them with technical and production possibilities according to the following criteria
MVP
Minimal Viable Product or must-have
Good
should-have
Desired
nice-to-have
In this phase, the customer can already balance the product development costs and make a rough estimation of engineering complexity.
Proof of Concept
As soon as requirements are settled, Proof of Concept (PoC) phase follows in order to prove that designed requirements can function as expected. For the pure software projects, this phase is optional.


Customer Decision
When having a PoC at hand, it is much easier to meet a decision or persuade your colleagues in order to proceed. In the Customer Decision ph ase, we align budget, legal issues, define deadlines and main milestones. In case the decision is negative, the customer has saved significant product development costs and can use PoC either for trade fair demonstrations or for further generation of ideas inside the company.
Product Development
Product Development phase is an aligned development lifecycle combining hardware, firmware and software components. As we are working in a high-security industry, we pay much attention to the security-driven approach and perform periodical security checks and standard compliance. Development is done with iterations, where after each iteration we perform a product demo in order to align the expectations with the customer. We set up delivery in a way, where customer can deploy the solution on his own, check its functionality and quality according to the provided functional and test documentation. Each iteration is released to the internal or test stores.


Release
For a final Release, certain preparations from both customer and CoreWillSoft side are required. These include marketing materials, legal compliance and documentation for stores and certificate authorities, eventual penetration testing through third-party agencies. The phase is complete as soon as official product launch takes place.
Maintenance
As each solution requires certain periodical Maintenance, this phase directly follows the release process. The customer can choose the options he would like to be covered by CoreWillSoft: Service Level Agreement (SLA), keeping solutions up to date and secure by regularly revising technical stack, security updates of the relevant components.


Further Enhancements
As successful products tend to evolve and customers start using them, new functionality requests emerge. Further Enhancements actually replicate the process starting from Business Analysis to Release and can be gracefully combined with main product creation and maintenance agreements.
Certificates & Memberships
Our Services
We build secure electronic access control solutions comprising:
- Scalable host systems
- Mobile apps for
- Access management
- Visitor management
- Secure hardware maintenance
- Mobile credentials
- Software tool chains for integrations as:
- Application Programming Interfaces (APIs)
- Software Development Kits (SDKs)
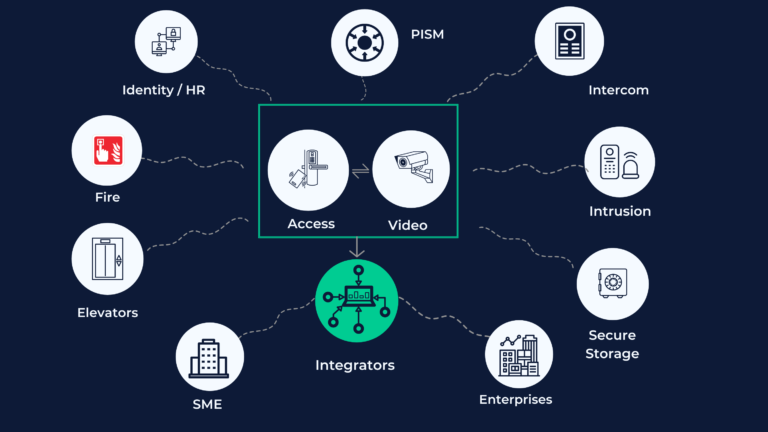
We connect any physical security systems with each other to satisfy your business needs. We provide connections between:
- Access control
- Video management software
- Intercom
- Identity management
- Credential management
- Intrusion
- Command control center software
Consulting services on various physical security topics:
- RFID technologies
- NFC
- BLE
- Card technologies as MIFARE® and Legic
- Security architecture and encryption
- Compliance with standards and protocols as OSS-SO, OSS-MA, PKOC / SCI
- Technological and product support by tenders